What is Opal + Terraform?
So, where exactly is Opal in all of this, and why would I care about Terraform?
At a high level, Terraform’s value lies in leveraging version control and code review to standardize access change, a core part of Opal’s philosophy in delegating reviews to those with the most context.
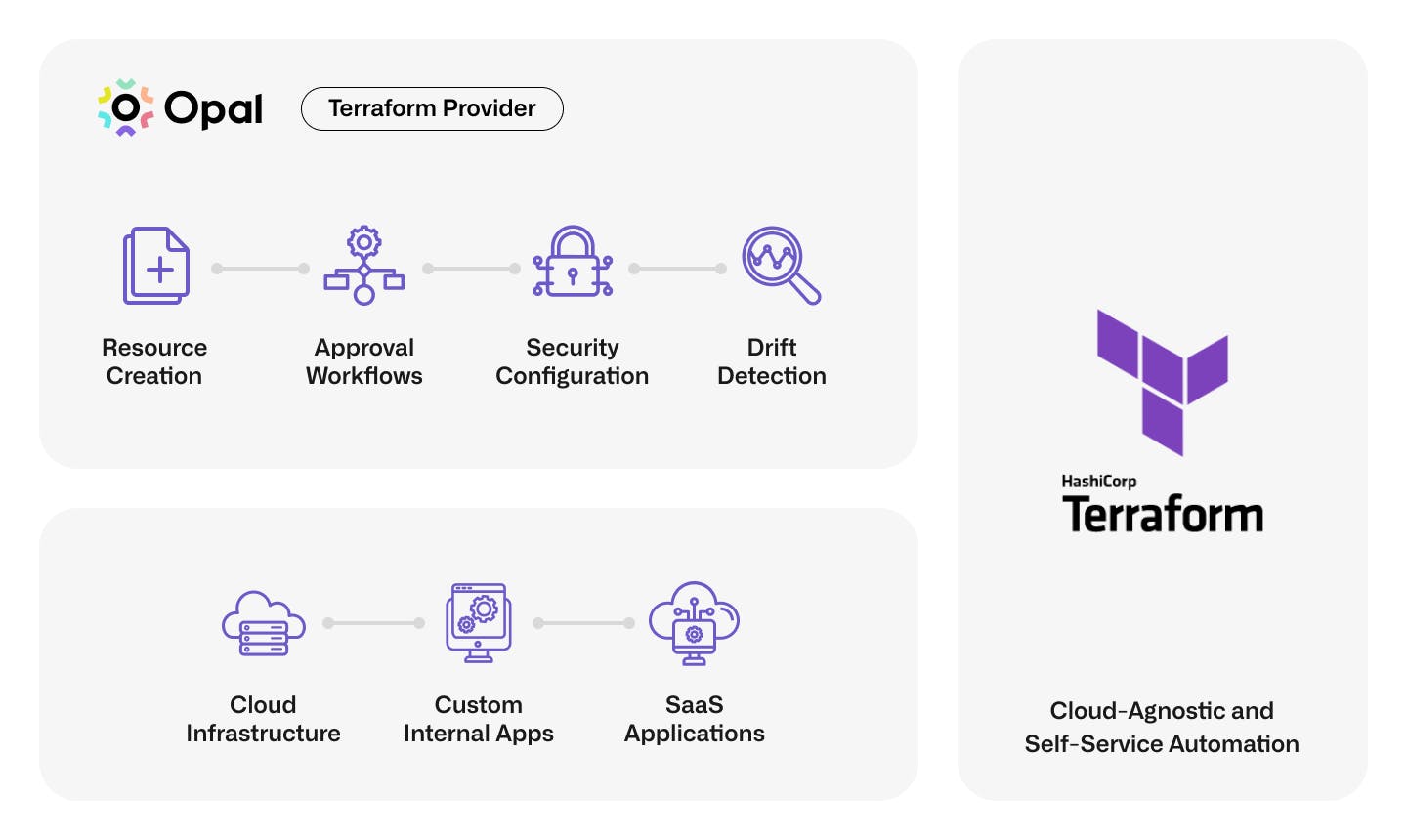
Our experience tells us that modern access management solutions must be extensible, which is why Opal takes an API-first approach. These APIs allow our customers to automate the ingestion of new resources and codify policies at scale, so operators can quickly integrate their custom internal applications and secure access to the cloud. Let’s explore this further in two areas, access reduction, and application onboarding.
Reducing your access footprint is hard. One critical way Opal helps solve this problem is its ability to break down larger group structures into smaller groups and individual resource-based entitlements based on need. The flip side of this approach is more objects means more policies. You want to maintain the granularity of access, but you cannot have operators manually configuring hundreds or thousands of policies either. Scalable configuration is where Opal's API shines! Customers don't have to sacrifice granular access to reduce operational overhead, and Terraform makes API automation accessible for all!
Security is a business accelerator, and trust has never been more critical than in today’s environment. The faster your security can move, the more confident your customers and employees will be. Many organizations already have cloud, internal tools, and identity provider deployments managed by infrastructure as code. Instead of manually entering this information in Opal’s UI, operators can programmatically share infrastructure states with Opal allowing migrations to happen in days instead of weeks or months. We’re doubling down on speed and supporting Terrafromer day zero to allow customers to bring existing Opal deployments under Terraform’s management in minutes.
A Terraform provider is only as good as its API. With significant investment and customer feedback on programmatic workflows, the time is right for a best-in-class Terraform provider to help our customers continue to adopt Opal! Teams can begin configuring Opal resources alongside the rest of their IT and infrastructure stacks. Let’s explore a few use cases!
Use Case: Accelerate Okta Access Requests
Okta is one of Opal’s most popular integrations, and we’ve learned progressive IT teams love Terraform and Okta. Don’t believe us; check the downloads page - the Okta provider has over nine million downloads! Okta infrastructure in Terraform is more predictable and easier to create and maintain for admins, which means faster onboarding times for new applications and happier end-users!
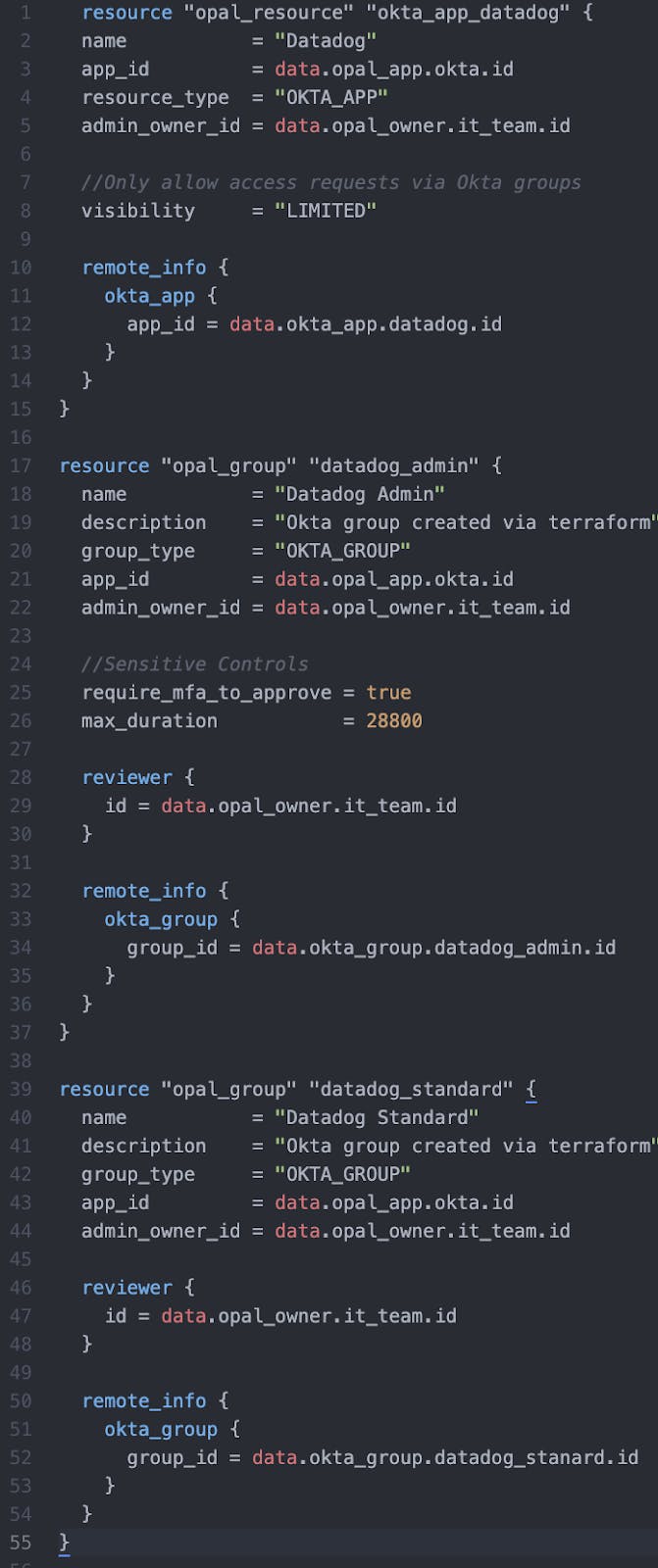
Now admins can extend their repositories and manage Opal alongside Okta in Terraform for the same benefit. Using Datadog as an example Okta app, enforcing requests to go through specific Okta groups, and making access to the admin role time-bound for one day is as simple as adding a few lines of declarative code in Opal’s provider.
Use Case: Fine-Grained Access for Cloud Infrastructure
At Opal, we are not shy about our commitment to protecting our customer’s most sensitive assets in the cloud. Hence, it’s only natural that our provider has first-class support for Opal’s cloud integrations. No JSON blobs here!
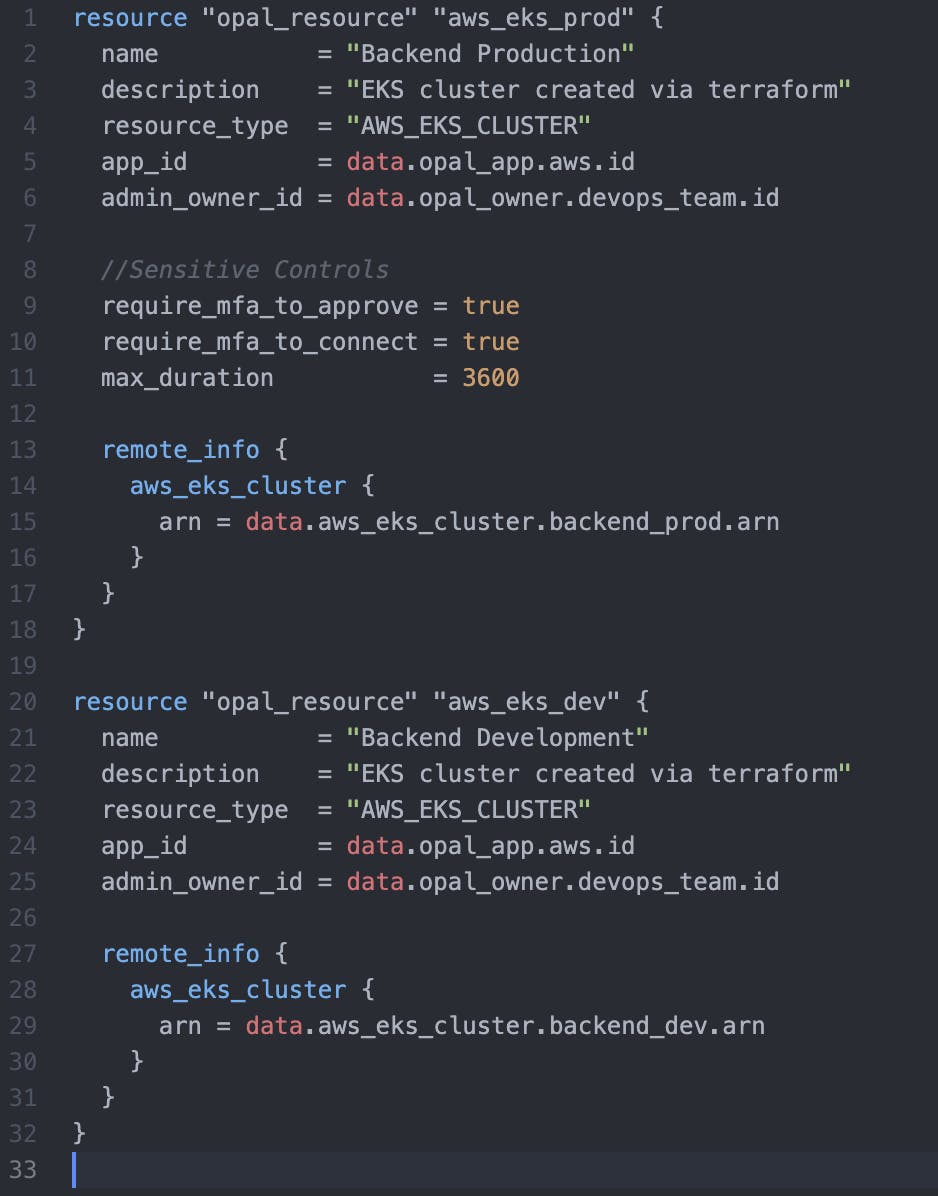
Your data sources or remote state can be shared directly with Opal, streamlining the onboarding process for resources in your cloud accounts and projects. Those who read our AWS series learned that EKS is one of many AWS resources we support natively inside Opal. Let’s expand that example with two EKS clusters, one that is marked sensitive for production and another that is a permissive development environment.
With Terraform, retrieving the identifiers and bringing both clusters under Opal’s management is easy. Most importantly, we can ensure that the production environment has MFA controls for approvals and credential issuance, with a maximum session duration of one hour to ensure continuous compliance for day-to-day operations.
Summary
Our aim with the Terraform provider is programmatic workflows that complement our user surfaces, such as Opal’s web interface and Slack commands. We believe certain activities should always require human interaction, like sensitive approvals or privileged onboarding of systems like AWS or Salesforce. Tasks that require automation can be easily modeled and understood in Terraform, and our other surfaces can help you do everything else!
