Table of contents
- What is an API?
- How does API work?
- Features of API
- Why would we need an API?
- Managing APIs
- API Security: Why is Important?
- Different methods for securing APIs
- API Key Authentication
- Access Control List Authorization
- What is Cherrybomb by Bussiness Logic Security Testing (BLST)?
- How does it work?
- Installation
- Usage
- Features
- Getting Started
- Home
- Settings
- Business Logic Section
- Uploading Files
- OpenAPI Specification
What is an API?
Application Programming Interface (API) is a software interface that allows two applications to interact with each other without any user intervention. API is a collection of software functions and procedures. In simple terms, API means a software code that can be accessed or executed.
In general, APIs define the rules that programmers must follow to interact with a programming language, a software library, or any other software tool.
How does API work?
Let's look at how API works with a basic example from everyday life. Assume you've gone to a restaurant for lunch or dinner. The server approaches you and hands you a menu card, which you can modify by specifying that you want a pizza with double cheese.
You will receive your order from the waiter when some time has passed. However, it is not as straightforward as it appears, since there is a process that takes place in the middle.
Because you will not go to the kitchen to pick up your order or tell the cooking crew what you want, the waiter will play a vital role in this situation.
API achieves the same thing by taking your request and, like a waiter, telling the system what you want and returning a response.
Features of API
- It provides a useful service (data, function, audience,.).
- It helps you to plan a business model.
- Simple, adaptable, and quick to implement.
- Measured and managed.
- Provides excellent developer help.
Why would we need an API?
Here are a few reasons to use API:
- API allows two separate software applications to communicate and exchange data.
- It makes it easier to embed content from any website or application.
- APIs can access app components. The delivery of services and information is more flexible.
- Content generated can be published automatically.
- It enables a consumer or an organization to personalize the content and services they use most frequently.
- Software needs to change over time, and APIs help to anticipate changes.
Managing APIs
As the world has grown more digital, so too has its reliance on APIs. The need for connected software has exploded, and APIs are everywhere.
This new reality brings endless possibilities, but it also brings challenges. Increased reliance on APIs means that they should run perfectly, every time. There are three key things you should start doing now to manage third-party APIs:
Comprehensive logging of third-party API activity - how many calls are being made and how long they are taking, how many errors are being returned, etc.
Monitoring and alerting - so you can identify issues before they affect users.
Implementing reliability features like automatic retries - API calls fail for many reasons and can often be immediately retried successfully.
API Security: Why is Important?
API security is about protecting the integrity of APIs, both the ones you own and the ones you use. What does that mean? Why is API security important?
Businesses use APIs to connect services and transfer data. The most significant data leaks are due to faulty, vulnerable, or hacked APIs, which can reveal medical, financial, and personal data to the general public. That said, not all data is created equal and does not have the same level of protection. Your strategy for securing APIs should depend on the type of data being recorded.
Different methods for securing APIs
The most common approaches to securing APIs are through the use of authentication and authorization mechanisms.
- Authentication is the process of verifying a user's identity, whereas authorization is the process of determining whether a person has access to a specific resource.
- OAuth is a common authentication method that allows users to safely log in to third-party apps using their existing credentials. OAuth is an industry-standard protocol that provides a secure, delegation-based mechanism for authentication and authorization.
- JSON Web Token is another popular authentication method (JWT).
- JWT is a JSON object-based standard that specifies a concise and self-contained method of sending information between parties.
API Key Authentication
- API keys are secret, each value that is used to authenticate and authorize API access.
- They're usually generated by the API provider and delivered to the API user.
API keys are a basic and simple way to secure an API, although they do have certain disadvantages.
They are static and cannot be revoked or changed.
API keys are typically passed in plain text as part of the request, which makes them susceptible to interception by third-parties.
Access Control List Authorization
- An access control list (ACL) is a set of permissions assigned to a specific user or group of users. When a user attempts to access a resource, the app examines the ACL to determine if the user has the required permissions.
- Role-based access control (RBAC) is another popular strategy. Users are given one or more roles, each with its own set of permissions, using RBAC.
- When a user tries to access a resource, the application checks to see if the user has the necessary role (or roles) and, if so, whether the role (or roles) have the necessary permissions.
What is Cherrybomb by Bussiness Logic Security Testing (BLST)?
Cherrybomb is a CLI tool that helps you avoid undefined user behavior by validating your API specifications.
- It validates API specifications through the various stages of API design.
- It is open-source, enabling support from both the OpenAPI and Rust communities.
- It supports the OpenAPI Specification, which is a standard for specifying how APIs work. It also supports HTTP logs, which can be used to debug API calls.
How does it work?
It takes an OAS file, runs several checks to ensure that everything is in order, and then provides a detailed table with any alerts discovered, pointing you to the specific problem and location to assist you in solving it quickly. It can also take your logs and look for errors in business logic.
Installation
Using cURL
Linux/MacOS:
curl cherrybomb.blstsecurity.com/install | /bin/bash
The script requires sudo permissions to move the cherrybomb bin into /usr/local/bin/.
Direct download
You can also download the binary file directly from HERE.
You DO NOT need to install Rust to use this binary file. If you use this method, run the command below to create a '.cherrybomb' directory in your home directory.
mkdir ~/.cherrybomb
Usage
After installing the CLI, verify it's working by running the below command
cherrybomb --version
An OpenAPI Specification file is a resource listing of your API that follows the OpenAPI Specification guidelines (OAS). Without access to source code, documentation, or network traffic inspection, the OAS establishes a standard, language-agnostic interface to RESTful APIs that allows humans and computers to discover and comprehend the service's capabilities.
cherrybomb oas --file --config --verbosity <0/1/2> --format --output
Example:
cherrybomb oas --file example-oas.json --verbosity 1
output example:
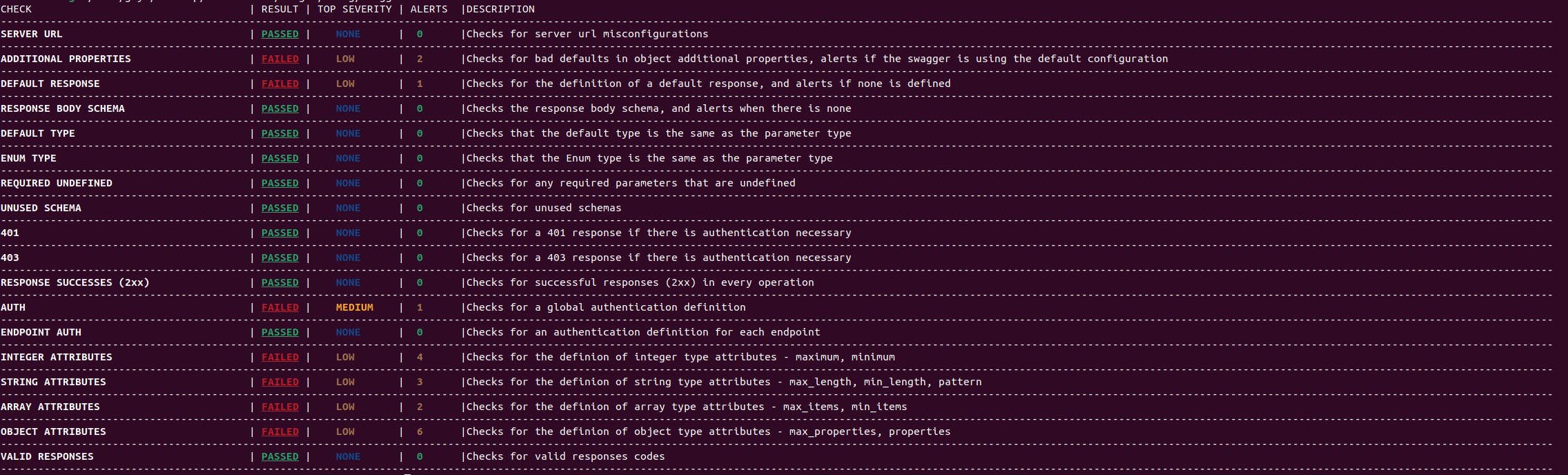
The parameter table accepts an OAS and produces a detailed description of each parameter in your app. You can use this table to get a list of the parameters, endpoints, and other data that an application instance has. You can use this information to decide which parameters need to be ordered for a future upgrade, to see if you have the prerequisites for a given function installed, and show an auditor or procurement team what you have installed.
- The name column contains the name of the parameter.
- This parameter's structure is described by the type object.
- In most cases, the status code is a success.
- Where the parameter is sent/received is indicated in the delivery methods column.
- The endpoints column indicates where the parameter appears in the document.
- The hierarchical object in the given JSON is described by the parents and children columns.
cherrybomb ep-table --file --name
Example:
cherrybomb oas --file example-oas.json --param-table
Table output example:
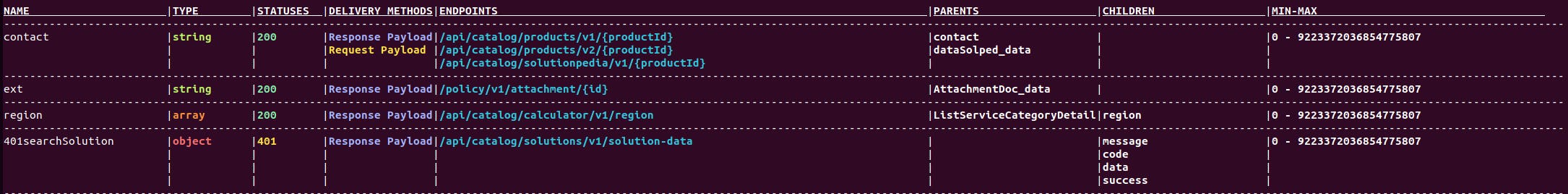
The endpoint table accepts an OAS and produces a detailed description of each endpoint in your app. You may use this table to see a list of all the endpoints that an application instance contains. You can use this information to decide which endpoints need to be ordered for a future update, to see if you have the prerequisites for a given function installed, and to show an auditor or procurement team what you have installed.
- The path column describes a specific endpoint's whole path.
- Operations is another name for HTTP method.
- Statuses refers to the status code that the endpoint can receive.
- This endpoint's header params column specifies which headers can be utilized.
- Query params are the parameters that appear in the GET request.
- Body params are the parameters which appear in POST's body request.
- Response params are the parameters that can appear in a response.
cherrybomb ep-table --file --name
Table output example:
Features
API Endpoint Mapper - Cherrybomb created an endpoint mapper with a developer-friendly interface that offers a graphical overview of your API and quick insights.
Params table - Create a visual API from your complex JSON specification files so that it can be filtered and examined as an indexable, searchable, and accessible table.
OAS Misconfiguration Checks - Find all the code bits or parameters in your API that aren't operating properly using the detailed information below.
Visualizer - Takes in the digest file from the mapper and visualizes the business logic flow of the application.
Getting Started
There are two ways to get started :
(The Fastest Way)- You can upload your Open API Specification to the main page After that, you'll be able to connect or create an account.
The conventional way to create an account is to go to the SignUp page and fill out your information, after which you will receive an email confirmation with instructions on how to log in to your account.
After you've made your account, the Dashboard page will provide you with a few options.
Home
Home page details all usage statistics.
- The Running Actions describe the next files to be uploaded.
- The number of OAS files uploaded.
- The number of map files uploaded.
- The total amount of domains and subdomains.
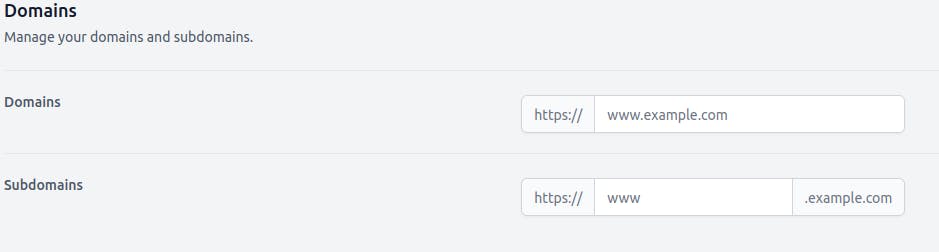
Settings
You'll be taken to the Settings tab after logging in. You can edit your personal information and change your username or email address here. Furthermore, you must first set up your domains and subdomains before using any of the services. This will make it easier for you to swap between your subdomains later.
Business Logic Section
Business logic, often known as business rules, is a set of standards that define how a business should function. These rules set the boundaries and criteria for how businesses create and process data, as well as how staff interact with consumers and other people.
In the software development lifecycle (SDLC) development process, BLST detects API flaws in the integration environment. DevOps and AppSec teams may use the automated security testing solution to discover Business Logic anomalies in APIs, generate an API flow map, and locate rogue endpoints. This increases system security while also allowing teams to shift left early in the CI/CD process.
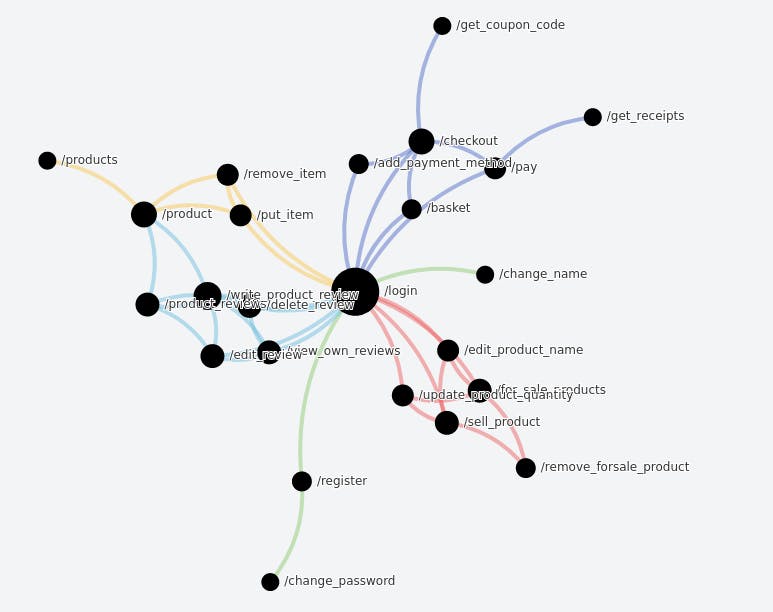
Network
Your API is mapped into a one-to-multi-connected vector using this network, also known as a "mapper." Because the schema is dependent on your log file, if an endpoint does not appear in your uploaded log, it will not appear here. Each point describes an endpoint as well as its relationship to other endpoints.
The goal of the mapper is to help you better understand how your application's business logic works. The biggest dot is the beginning of all the traffic.
Example:
Uploading Files
The Map file should include all your HTTP logs in a JSON format up to one gigabyte. The log file will be used to create a map of your entire API network.
Session Structure:
[{ "session":[{ request:String, response:String }] }]
For the mapper to work effectively, the structure of a single session log should look like this.
How to Upload your Logs file?
- In the Network Section, click on the "upload Map" button.
- After that, drag and drop your file into the proper location.
- After you have uploaded your file, you have to choose where to save your data.
- You have the choice to update an existing log file by just clicking on the second option and choosing the log file you want to modify.
- Take into consideration that this option will only add new endpoints to the existing structure and not remove the older one.
Running actions can take up to one minute to upload your file.
OpenAPI Specification
A resource listing of your API that adheres to the OpenAPI Specification is what an OpenAPI Specification file is (OAS). Without access to source code, documentation, or network traffic analysis, the OAS establishes a standard, language-agnostic interface to RESTful APIs that allows both humans and machines to explore and comprehend the capabilities of the service. The Params, OAS Checker, and Endpoint table are all generated using the swagger file.
BLST takes an OAS file, runs a number of checks to ensure that everything is in order, and then provides a thorough table with any alerts discovered, pointing you to the specific problem and place to assist you in solving it quickly.
Do you want to deep dive into how OpenAPI Specification works? CLICK HERE.
