Kubernetes configuration files and object definitions are most commonly written in YAML files. As these files define how things run on our clusters, improving YAML file security and flow is important. Among the most crucial things, our files need to be audited and validated before being applied to our Kubernetes clusters. Misconfigurations such as escalated container privileges and missing keys have to be avoided at all costs, as these can open access to unauthorized users.
Luckily, there are many Kubernetes security tools that have been emerging such as Kubescape and ValidKube. In order to take advantage of these tools, they should be implemented in your Kubernetes workflow - especially in the case of ValidKube, as will be described.
In today article, we are focusing on ValidKube and how to apply the tool.
ValidKube
ValidKube is a new open-source tool that combines several tools to make it easier to validate, clean, and secure Kubernetes YAML configuration files.
ValidKube from Komodor which is a free tool used to validate and enforce Kubernetes best practices on your manifests and configuration files, folding in multiple open-source tools.
ValidKube tool is used to:
- Validate configuration files
- Clean manifest files
- Scan and secure your YAML files by ensuring best practice
You don't need special skills or cram commands just to use ValidKube, as it is an online web tool.
All you need to do is paste your YAML contents and choose if you want to clean, audit, secure, or validate the YAML contents.
In this tutorial, you will learn how to clean and secure your manifests using ValidKube and Kubescape.
This tutorial will cover the following points
- Scanning and securing your manifests using Validkube
- How to audit and validate your YAML files using Kubescape, and scanning clusters against security frameworks
Conclusion
Prerequisites
You need a running Kubernetes cluster, as well as the KUBECONFIG for it.
Scanning and securing your manifests using Validkube
ValidKube is great at catching common Kubernetes manifest misconfigurations, such as missing keys and null values. You can validate any type of Kubernetes resource or object. In this tutorial, I will show you how to validate and secure a deployment object. Here are the contents of a sample deployment:
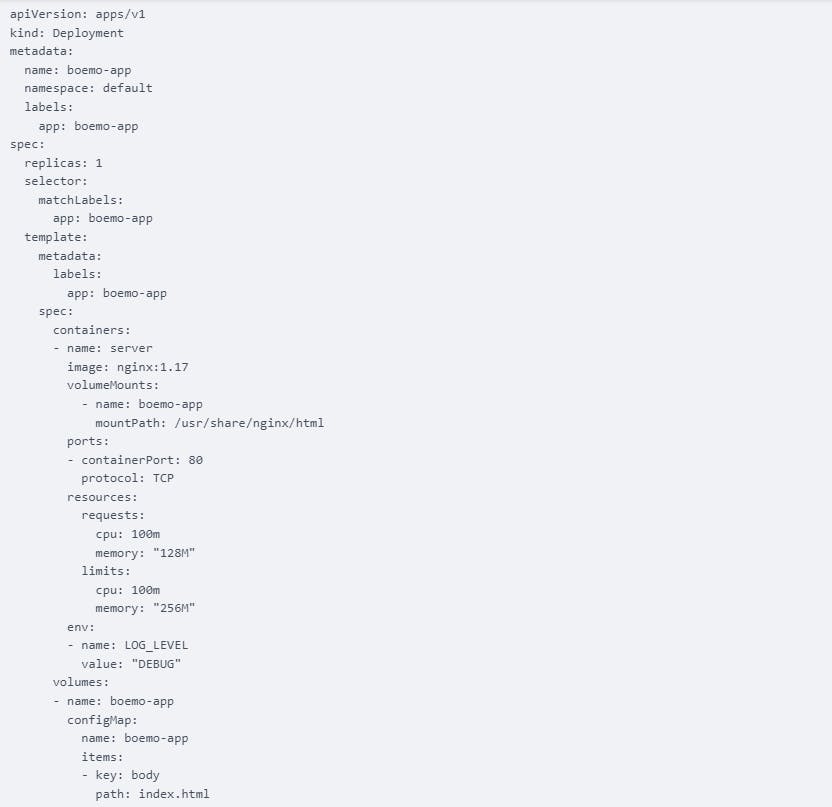
Copy the above YAML and paste it on ValidKube, click on the validate text button to validate the YAML file:
When you click on the validate button ValidKube immediately outputs the results, which should appear on the right hand side showing the following:

But, If I enter an invalid value on the replica field, changing it from 1 to a string, ValidKube will give out the expected value type which is the integer type:
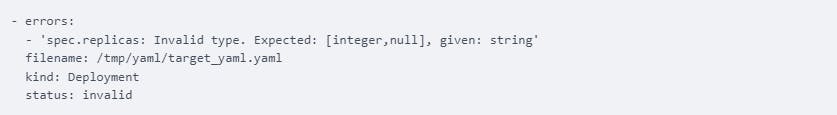
Validkube uses Kubeval to validate the deployment object. Kubeval is a command line that validates YAML files by comparing them to Kubernetes generated API schemas.
Cleaning a YAML file using ValidKube
Next, click on the clean text button on ValidKube to clean up the YAML file. Under the hood, ValidKube uses Kube-neat to format, reorganize, and remove clutter from the provided YAML file. Here are the results of the cleaning procedure using kube-neat.
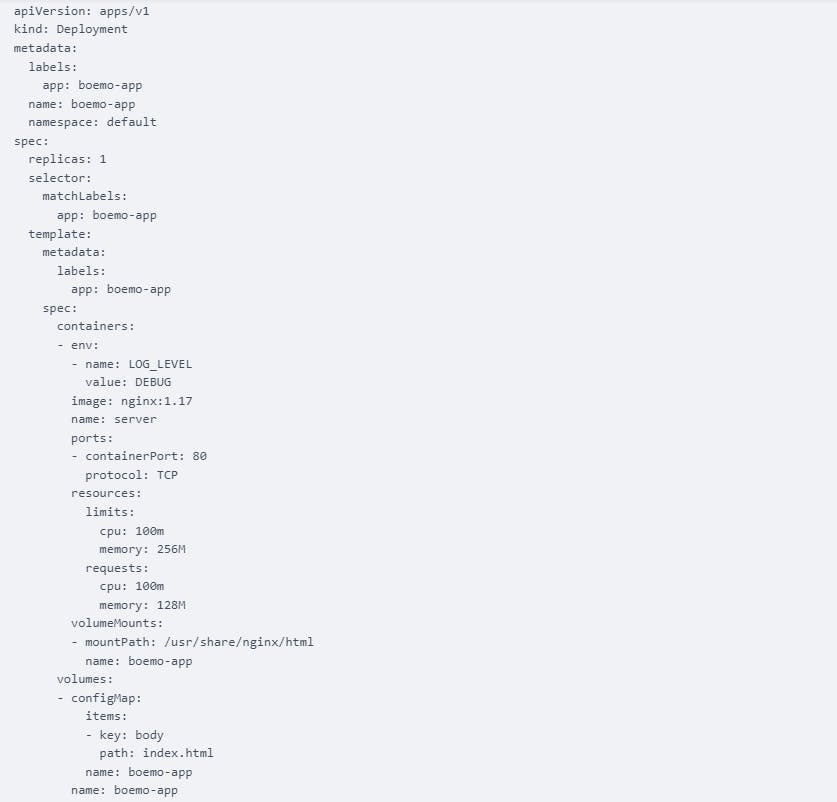
ValidKube has cleaned the deployed YAML file by formatting the contents and added the volumeMount which was missing. This process of linting, or removing clutter and formatting files the right way makes it easy for code reviewers because they won't be reviewing unnecessary code lines.
Carrying out security analysis using ValidKube
ValidKube uses Trivy from AquaSecurity to check security vulnerabilities. Trivy is a tool that scans images and clusters looking for security vulnerabilities. Here are the security scan results after clicking on the secure text button on our sample deployment file from earlier:

The results will start by summing up the failure and specifying the detected misconfiguration together with its description:
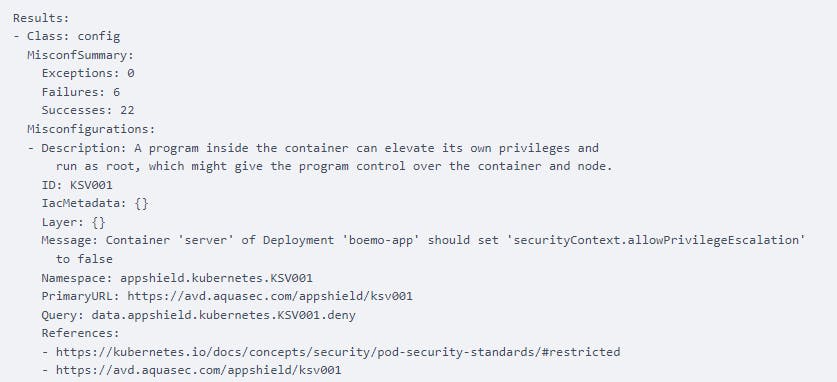
Next, you will get a suggested solution to the detected vulnerabilities:
Resolution: Set 'set containers[].securityContext.allowPrivilegeEscalation' to 'false'. Severity: MEDIUM Status: FAIL Title: Process can elevate its own privileges Type: Kubernetes Security Check
- Description: The container should drop all default capabilities and add only those
that are needed for its execution.
ID: KSV003
IacMetadata: {}
Layer: {}
Message: Container 'server' of Deployment 'boemo-app' should add 'ALL' to 'securityContext.capabilities.drop'
Namespace: appshield.kubernetes.KSV003
PrimaryURL: avd.aquasec.com/appshield/ksv003
Query: data.appshield.kubernetes.KSV003.deny
References:
- kubesec.io/basics/containers-securitycontex..
- avd.aquasec.com/appshield/ksv003 Resolution: Add 'ALL' to containers[].securityContext.capabilities.drop. Severity: LOW Status: FAIL Title: Default capabilities not dropped Type: Kubernetes Security Check
- Description: '''runAsNonRoot'' forces the running image to run as a non-root user
to ensure least privileges.'
ID: KSV012
IacMetadata: {}
Layer: {}
Message: Container 'server' of Deployment 'boemo-app' should set 'securityContext.runAsNonRoot'
to true
Namespace: appshield.kubernetes.KSV012
PrimaryURL: avd.aquasec.com/appshield/ksv012
Query: data.appshield.kubernetes.KSV012.deny
References:
- kubernetes.io/docs/concepts/security/pod-se..
- avd.aquasec.com/appshield/ksv012 Resolution: Set 'containers[].securityContext.runAsNonRoot' to true. Severity: MEDIUM Status: FAIL Title: Runs as root user Type: Kubernetes Security Check
- Description: An immutable root file system prevents applications from writing
to their local disk. This can limit intrusions, as attackers will not be able
to tamper with the file system or write foreign executables to disk.
ID: KSV014
IacMetadata: {}
Layer: {}
Message: Container 'server' of Deployment 'boemo-app' should set 'securityContext.readOnlyRootFilesystem'
to true
Namespace: appshield.kubernetes.KSV014
PrimaryURL: avd.aquasec.com/appshield/ksv014
Query: data.appshield.kubernetes.KSV014.deny
References:
- kubesec.io/basics/containers-securitycontex..
- avd.aquasec.com/appshield/ksv014 Resolution: Change 'containers[].securityContext.readOnlyRootFilesystem' to 'true'. Severity: LOW Status: FAIL Title: Root file system is not read-only Type: Kubernetes Security Check
- Description: Force the container to run with user ID > 10000 to avoid conflicts
with the host's user table.
ID: KSV020
IacMetadata: {}
Layer: {}
Message: Container 'server' of Deployment 'boemo-app' should set 'securityContext.runAsUser'
10000 Namespace: appshield.kubernetes.KSV020 PrimaryURL: avd.aquasec.com/appshield/ksv020 Query: data.appshield.kubernetes.KSV020.deny References:
ValidKube will categorize the level of impact the vulnerability can make if exploited. The levels range is Low, Medium and High. Vulnerabilities that are classified as high should be solved immediately, but you should not forget about the lower-classified issues either. They will be marked as failures alongside your other results:

Auditing YAML files with ValidKube
For the auditing procedure, ValidKube uses the Fairwinds Polaris tool which scans clusters looking for misconfigurations. Here are the results of the audit scan after clicking on the audit button:
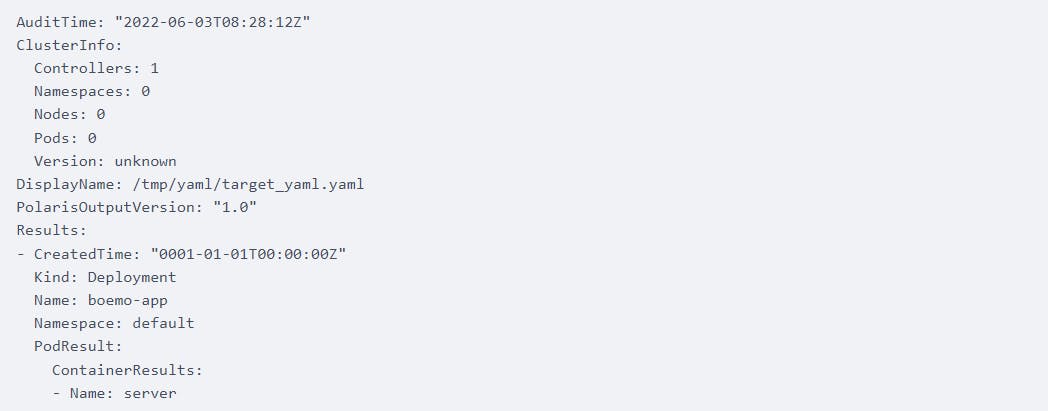
ValidKube will categorize issues found in the audit into efficiency and security groups. If a vulnerability belongs to the efficiency category it means that it affects the cluster's performance. For example, the followin report notes efficiency issues around CPU limits and requests not being configured:
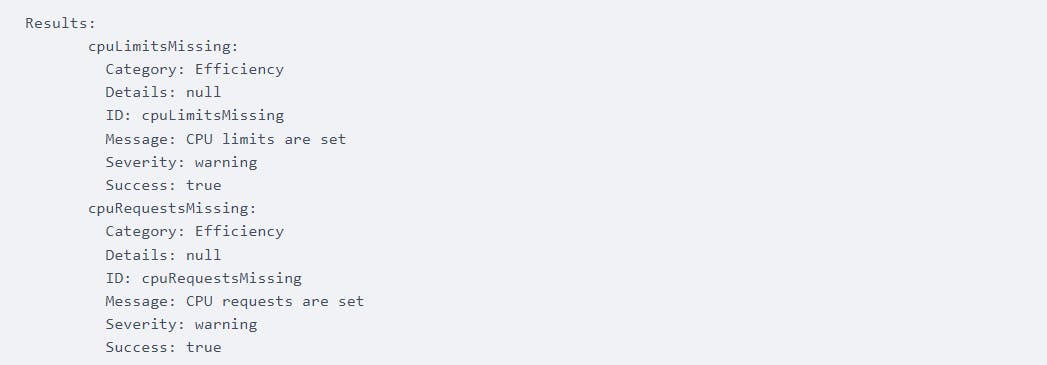
Alongside the efficiency issues, you will get notified if your container has dangerous capabilities:
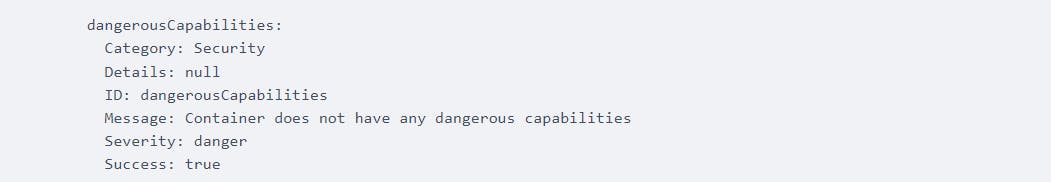
All fields that do not have values will be detected and displayed:

Conclusion ValidKube is the tool that you should use to combat security vulnerabilities on a daily basis. Prevention is better than the cure.
ValidKube will surely improve your productivity and workflow as it audits, secures and validates files you pass to it, and bundles multiple useful scans.
